Webwatcher, a term that conjures images of digital shadows and unseen eyes, has become a ubiquitous presence in our online lives. From parental controls to employee monitoring and cybersecurity, webwatcher software plays a multifaceted role in shaping our digital experiences.
Table of Contents
The concept of webwatcher software encompasses a range of technologies designed to monitor online activity, ranging from simple website blocking to sophisticated keystroke logging and screen recording. Understanding the complexities of webwatcher software requires navigating the delicate balance between security, privacy, and ethical considerations.
Webwatcher Definition and Purpose
Webwatcher software refers to applications designed to monitor online activity on computers or mobile devices. It functions by recording and logging various aspects of internet usage, including websites visited, applications used, emails sent and received, and even keystrokes entered.
Webwatcher software serves a variety of purposes, ranging from parental control and employee monitoring to cybersecurity. These applications can be used to ensure responsible internet use, protect sensitive information, and even prevent illegal activities.
Parental Control
Parental control software aims to protect children from inappropriate content and online dangers. It can be used to block access to specific websites, restrict online time, and monitor communication with other users. Examples of features commonly included in parental control software are:
- Website filtering: Blocking access to websites containing explicit content, violence, or other inappropriate material.
- Time limits: Setting limits on how much time children can spend online.
- App blocking: Preventing the use of specific applications deemed unsuitable for children.
- Location tracking: Monitoring the child’s physical location through GPS tracking.
- Communication monitoring: Reviewing messages sent and received through instant messaging, social media, and email.
Employee Monitoring
Employee monitoring software is used by employers to track employee productivity, prevent data breaches, and ensure compliance with company policies. Some of the common features of employee monitoring software include:
- Keystroke logging: Recording every keystroke entered on a computer, providing insights into employee activity and potential security threats.
- Website and application tracking: Monitoring websites visited and applications used during work hours, ensuring employees focus on assigned tasks.
- Email monitoring: Reviewing employee emails for compliance with company policies and detecting potential security risks.
- Screen recording: Capturing screenshots or video recordings of the employee’s computer screen, allowing employers to monitor activity and identify potential misconduct.
- Internet usage monitoring: Tracking the amount of time spent on the internet and websites visited, providing data on employee productivity and potential distractions.
Cybersecurity
Webwatcher software can be used to enhance cybersecurity by detecting and preventing malicious activity. Examples of cybersecurity applications of webwatcher software include:
- Malware detection: Monitoring for suspicious activity and identifying potential malware infections.
- Phishing detection: Identifying and blocking phishing attempts designed to steal sensitive information.
- Data leakage prevention: Monitoring for unauthorized access to sensitive data and preventing its leakage.
- Network monitoring: Tracking network traffic and identifying potential security threats.
- Intrusion detection: Detecting and responding to unauthorized access attempts to computer systems.
Ethical Considerations
The use of webwatcher software raises significant ethical concerns. These concerns primarily revolve around privacy, transparency, and consent.
- Privacy: Webwatcher software can collect vast amounts of personal data, raising concerns about privacy violations. Individuals may not be aware of the extent to which their online activity is being monitored, leading to potential misuse of their personal information.
- Transparency: The use of webwatcher software should be transparent, with individuals informed about the monitoring practices and the purpose of data collection. Clear and concise disclosure is essential to ensure informed consent and respect for individual privacy.
- Consent: Obtaining explicit consent from individuals before monitoring their online activity is crucial. For example, parents should inform their children about the use of parental control software and its implications for their privacy. Similarly, employers should inform employees about monitoring practices and the reasons behind them.
Types of Webwatcher Software
Webwatcher software can be broadly categorized based on its primary functionality. Understanding these categories can help you choose the right type of software for your specific needs.
Types of Webwatcher Software
Webwatcher software can be categorized based on its primary functionality, and each type comes with its own advantages and disadvantages. Here are some common types of webwatcher software:
- Parental Control Software: This type of software is designed to help parents monitor their children’s online activity. It typically includes features such as website blocking, time limits, and content filtering. Examples include:
- Qustodio
- Bark
- Net Nanny
Advantages:
- Provides parents with valuable insights into their children’s online behavior.
- Helps protect children from inappropriate content and online risks.
- Can be used to set healthy online habits.
Disadvantages:
- Can be intrusive and may violate children’s privacy.
- May not be effective against sophisticated methods of bypassing restrictions.
- Requires ongoing monitoring and adjustments.
- Employee Monitoring Software: This type of software is used by employers to monitor their employees’ online activity while at work. It can track website visits, emails, and other activities. Examples include:
- Teramind
- Hubstaff
- Time Doctor
Advantages:
- Helps ensure employee productivity and prevent misuse of company resources.
- Can provide insights into employee behavior and performance.
- Can help prevent data breaches and other security risks.
Disadvantages:
- Can raise privacy concerns and erode trust between employers and employees.
- May be seen as intrusive and discouraging of creativity and innovation.
- Requires careful implementation and communication to avoid legal issues.
- Social Media Monitoring Software: This type of software is used to track and analyze social media activity. It can be used by businesses to monitor brand mentions, identify influencers, and analyze public sentiment. Examples include:
- Hootsuite
- Brand24
- Mention
Advantages:
- Provides valuable insights into public opinion and social media trends.
- Helps businesses monitor their brand reputation and identify potential crises.
- Can be used to track competitor activity and identify opportunities for growth.
Disadvantages:
- Can be overwhelming to manage large amounts of data.
- May require specialized skills to interpret the results effectively.
- Can be expensive, especially for advanced features.
- Security Monitoring Software: This type of software is designed to detect and prevent cyber threats. It can monitor network traffic, identify malicious activity, and block suspicious connections. Examples include:
- Symantec Endpoint Protection
- Kaspersky Endpoint Security
- Sophos Central
Advantages:
- Provides a crucial layer of protection against cyber threats.
- Can help prevent data breaches and other security incidents.
- Can provide real-time alerts and notifications.
Disadvantages:
- Can be complex to configure and manage.
- May require regular updates and maintenance.
- Can sometimes generate false positives, leading to unnecessary alerts.
Webwatcher Features and Capabilities

Webwatcher software offers a range of features designed to monitor and control online activity. These features can be used for various purposes, including parental control, employee monitoring, and personal safety. However, the use of these features raises concerns about user privacy and security.
Website Blocking
Website blocking is a common feature of webwatcher software. It allows users to restrict access to specific websites or categories of websites. This can be useful for preventing children from accessing inappropriate content or employees from wasting time on social media.
Website blocking typically works by creating a list of blocked websites or using pre-defined categories. When a user attempts to access a blocked website, the webwatcher software intercepts the request and prevents the website from loading. Some webwatcher software also allows users to set time limits for website access.
Keystroke Logging
Keystroke logging is a feature that records every keystroke made on a device. This information can be used to monitor what users are typing, including passwords, emails, and other sensitive data.
Keystroke logging works by capturing keystrokes as they are entered. The captured data is typically stored in a log file that can be accessed by the webwatcher software. This feature can be used for various purposes, such as monitoring employee productivity or detecting fraudulent activity. However, it can also be used to invade user privacy.
Screen Recording, Webwatcher
Screen recording captures the entire screen activity, including the content displayed, mouse movements, and keystrokes. This feature can be used to monitor employee activity, record online tutorials, or capture gameplay footage.
Screen recording works by capturing the screen content at regular intervals and saving it to a video file. The video file can then be reviewed to see what happened on the screen. This feature can be used for various purposes, but it can also be used to invade user privacy.
Location Tracking
Location tracking is a feature that allows users to monitor the location of a device. This can be useful for finding a lost device, tracking a child’s location, or monitoring employee movements.
Location tracking typically works by using GPS data, cellular network data, or Wi-Fi data to determine the location of a device. The location data can be displayed on a map or used to generate reports. This feature can be useful for various purposes, but it can also be used to invade user privacy.
Legal and Ethical Implications
Webwatcher software, while offering various benefits, also raises significant legal and ethical concerns, particularly in relation to privacy, consent, and the potential for misuse. Understanding the legal frameworks and ethical considerations associated with webwatcher software is crucial for both users and developers.
Legal Frameworks
The legality of webwatcher software use varies across jurisdictions and depends on factors such as the purpose of monitoring, the age of the individual being monitored, and the nature of the data being collected. Generally, laws governing webwatcher software fall under broader privacy and data protection regulations.
- United States: The Electronic Communications Privacy Act (ECPA) and the Children’s Online Privacy Protection Act (COPPA) are key legislation governing electronic surveillance and data collection. These laws require explicit consent for monitoring and restrict the use of webwatcher software for certain purposes, such as monitoring employees without their knowledge or consent.
- European Union: The General Data Protection Regulation (GDPR) imposes strict rules on data collection, processing, and storage. The GDPR requires explicit consent for data processing, data minimization, and the right to access, rectify, or erase personal data.
- Other Jurisdictions: Many countries have similar laws governing data privacy and surveillance. For example, Canada’s Personal Information Protection and Electronic Documents Act (PIPEDA) and Australia’s Privacy Act 1988 regulate data collection and use.
Ethical Considerations
Beyond legal frameworks, ethical considerations play a vital role in determining the appropriate use of webwatcher software.
- Employee Monitoring: Monitoring employees’ online activities can raise concerns about privacy and trust. Ethical use of webwatcher software in the workplace requires transparency, clear policies, and a focus on legitimate business interests.
- Parental Control: While webwatcher software can be valuable for protecting children online, it’s crucial to strike a balance between safety and privacy. Parents should engage in open communication with their children about online safety and use webwatcher software responsibly.
- Data Privacy: The collection and storage of personal data through webwatcher software raises concerns about data security and misuse. It’s essential to ensure data is collected and stored securely and only for legitimate purposes.
Unethical or Illegal Use
The use of webwatcher software can be considered unethical or illegal in various scenarios.
- Monitoring without Consent: Using webwatcher software to monitor individuals without their knowledge or consent, particularly in personal contexts, is generally unethical and often illegal.
- Misuse of Data: Collecting and using personal data obtained through webwatcher software for unauthorized purposes, such as harassment, blackmail, or identity theft, is unethical and illegal.
- Violation of Privacy: Surveillance of individuals’ online activities without legitimate justification, such as monitoring employees’ personal communications or tracking children’s online movements without a clear safety concern, can violate privacy rights.
Webwatcher Software and User Privacy
Webwatcher software, while offering benefits for monitoring online activity, raises significant concerns about user privacy. The potential for misuse and the inherent nature of such software can lead to various privacy violations, making it crucial to understand the implications and navigate these challenges responsibly.
Transparency and Consent in Webwatcher Software Use
Transparency and consent are paramount in addressing the privacy concerns associated with webwatcher software. Users should be fully informed about the software’s capabilities, data collection practices, and how their information will be used.
- Explicit Consent: Clear and explicit consent should be obtained from individuals before installing or using webwatcher software. This consent should be informed, meaning users understand the software’s functions and potential implications for their privacy.
- Data Collection Disclosure: Users should be informed about the types of data collected, such as browsing history, website visits, app usage, and communication content. The purpose of data collection should be clearly Artikeld.
- Data Retention Policies: Transparency regarding data retention periods is crucial. Users should know how long their data will be stored and how it will be used after the monitoring period.
- Access and Control: Users should have access to the data collected by the software and the ability to modify or delete it. They should also have the right to withdraw their consent at any time.
Best Practices for Protecting User Privacy
Protecting user privacy while utilizing webwatcher software requires a proactive approach that prioritizes transparency, consent, and responsible use.
- Use Only for Legitimate Purposes: Webwatcher software should be used only for legitimate purposes, such as monitoring children’s online activity or protecting company data. It should not be used for surveillance or unauthorized monitoring.
- Minimize Data Collection: The software should be configured to collect only the necessary data. Unnecessary data collection should be avoided to minimize privacy risks.
- Data Encryption: Sensitive data collected by the software should be encrypted to prevent unauthorized access and protect user privacy.
- Regular Privacy Audits: Organizations and individuals using webwatcher software should conduct regular privacy audits to ensure compliance with privacy regulations and best practices.
- Educate Users: Users should be educated about the potential privacy risks associated with webwatcher software and how to protect themselves.
Security Concerns with Webwatcher Software
While webwatcher software offers valuable monitoring and control capabilities, it also introduces security vulnerabilities that require careful consideration. Understanding these risks and implementing appropriate mitigation strategies is crucial for protecting both the target user’s privacy and the overall security of the system.
Data Breaches
Webwatcher software stores sensitive data, including browsing history, website visits, and potentially personal information. This data is susceptible to breaches, which could expose confidential information to unauthorized individuals.
- Weak security measures: Inadequate password protection, insufficient encryption, and outdated software can create vulnerabilities that attackers can exploit.
- Data storage practices: The way data is stored and managed can impact its security. For instance, storing data on insecure servers or using inadequate backup procedures can increase the risk of data breaches.
- Insider threats: Employees or individuals with access to the webwatcher software’s backend infrastructure could potentially misuse their privileges to access or steal data.
Malware Infections
Webwatcher software, like any software, can be vulnerable to malware infections. If the software itself is compromised, attackers could gain control over the monitoring system, potentially accessing and manipulating data or even using it to launch further attacks.
- Software vulnerabilities: Exploitable flaws in the webwatcher software’s code can allow malware to gain access and execute malicious commands.
- Third-party dependencies: Webwatcher software may rely on third-party components or libraries, which could have their own vulnerabilities that attackers can exploit.
- Phishing attacks: Attackers can trick users into installing malicious software disguised as legitimate updates or extensions for the webwatcher software.
Unauthorized Access
Unauthorized individuals could gain access to the webwatcher software, compromising the target user’s privacy and potentially causing harm.
- Credential theft: Attackers can steal login credentials through phishing attacks, brute-force attempts, or other methods, allowing them to access the webwatcher software and its data.
- Weak authentication: If the webwatcher software uses weak authentication methods, such as simple passwords or easily guessable usernames, attackers can gain access more easily.
- Misconfigured access controls: Improperly configured access controls can allow unauthorized individuals to access the webwatcher software and its data.
Webwatcher Software and Cybersecurity
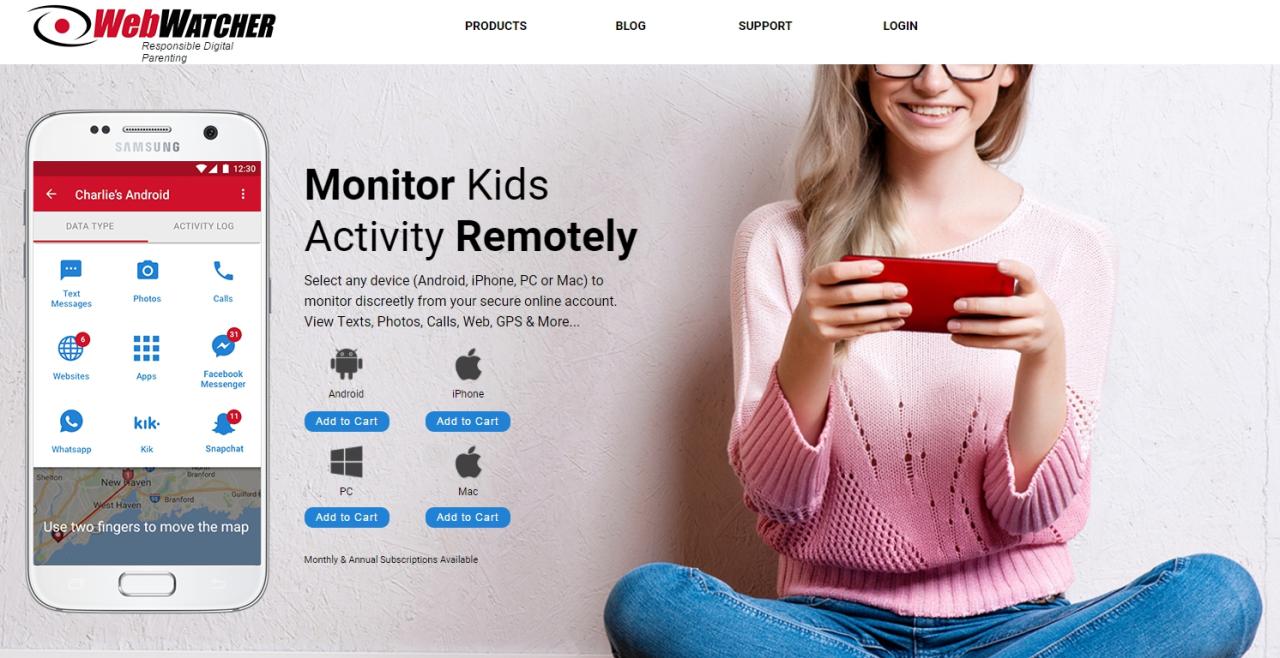
Webwatcher software, designed primarily for parental control and employee monitoring, can also play a role in cybersecurity. While not a primary cybersecurity tool, its features can contribute to detecting and preventing malicious activity, especially in home and small business environments.
Detection of Malicious Activity
Webwatcher software can help detect malicious activity by monitoring internet usage patterns.
- It can track websites visited, files downloaded, and applications used, potentially identifying suspicious activity that deviates from typical user behavior.
- Webwatcher software can also monitor for malware-related activity, such as attempts to access sensitive data or unusual communication patterns.
Prevention of Malicious Activity
Webwatcher software can contribute to preventing malicious activity by:
- Blocking access to known malicious websites and phishing sites, thus preventing users from falling victim to online scams or malware infections.
- Restricting the installation of potentially harmful applications, reducing the risk of malware infiltration through software downloads.
Effectiveness in Protecting Against Cyber Threats
While webwatcher software can offer some level of protection against cyber threats, its effectiveness is limited.
- It relies on pre-existing databases of known malicious websites and applications, which may not be comprehensive enough to catch all emerging threats.
- Sophisticated malware can evade detection by webwatcher software, especially if it uses techniques like social engineering or zero-day exploits.
- Webwatcher software is not a substitute for comprehensive cybersecurity measures, such as firewalls, antivirus software, and user education.
Alternative Solutions to Webwatcher Software
While webwatcher software offers a range of features for parental control, employee monitoring, and cybersecurity, alternative solutions provide different approaches with varying benefits and drawbacks. These alternatives can be more flexible, privacy-focused, or cost-effective, depending on the specific needs and goals.
Parental Control Alternatives
Parental control alternatives aim to create a safer online environment for children without resorting to constant monitoring.
- Open Communication and Education: Establishing open communication with children about online safety, responsible internet usage, and the potential risks is crucial. This approach fosters trust and empowers children to make informed decisions.
- Content Filtering and Blocking: Parental control features built into web browsers, operating systems, and internet service providers offer a level of content filtering and website blocking. These tools can restrict access to inappropriate websites and limit online time.
- Parental Guidance Software: Software like Google Family Link and Microsoft Family Safety allows parents to set screen time limits, block specific apps and websites, and track their child’s location.
- Family Tech Contracts: Establishing clear rules and agreements regarding internet usage, device access, and online behavior can foster responsible online habits and prevent conflicts.
Employee Monitoring Alternatives
Alternative solutions to employee monitoring software aim to build trust and accountability without intrusive surveillance.
- Performance Management Systems: Implementing robust performance management systems with clear goals, regular feedback, and opportunities for professional development can encourage productivity and accountability.
- Time Tracking and Project Management Tools: Utilizing time tracking and project management tools like Asana or Trello allows employees to track their progress, manage tasks efficiently, and demonstrate their work output.
- Open Communication and Trust: Establishing open communication with employees about expectations, responsibilities, and the importance of ethical online behavior fosters trust and reduces the need for constant monitoring.
Cybersecurity Alternatives
Cybersecurity alternatives focus on proactive measures to prevent cyber threats and protect sensitive data.
- Security Awareness Training: Educating employees about cybersecurity best practices, phishing scams, malware threats, and social engineering tactics can significantly reduce the risk of cyberattacks.
- Multi-Factor Authentication: Implementing multi-factor authentication for user accounts adds an extra layer of security, requiring users to provide multiple forms of verification before granting access.
- Strong Passwords and Password Managers: Encouraging the use of strong, unique passwords for different accounts and utilizing password managers to store and manage these credentials enhances account security.
- Regular Security Audits and Updates: Conducting regular security audits to identify vulnerabilities and implementing timely software updates helps to mitigate security risks.
Future of Webwatcher Software
The landscape of webwatcher software is poised for significant transformation, driven by advancements in technology and evolving societal needs. Emerging technologies like artificial intelligence (AI) and machine learning (ML) are set to reshape the capabilities and applications of webwatcher software, impacting online surveillance and cybersecurity.
Impact of Emerging Technologies
The integration of AI and ML into webwatcher software promises to revolutionize its capabilities. AI-powered webwatcher software can analyze vast amounts of data in real-time, identifying patterns and anomalies that might otherwise go unnoticed. This enables more accurate and proactive monitoring of online activity.
- Enhanced Threat Detection: AI algorithms can learn from past threats and identify new, emerging threats, providing a more robust defense against cyberattacks.
- Personalized Monitoring: AI can personalize webwatcher software, tailoring its monitoring capabilities to individual user needs and preferences.
- Automated Response: AI can automate certain tasks, such as blocking access to harmful websites or reporting suspicious activity, freeing up human resources for more complex tasks.
Future Role in Online Surveillance and Cybersecurity
Webwatcher software is expected to play an increasingly vital role in online surveillance and cybersecurity. The growing complexity of online threats and the rise of sophisticated cyberattacks necessitate advanced monitoring and security solutions.
- Proactive Threat Mitigation: Webwatcher software can proactively identify and mitigate potential threats before they materialize, reducing the risk of cyberattacks.
- Improved Incident Response: AI-powered webwatcher software can analyze data in real-time, providing valuable insights that can be used to improve incident response times and reduce the impact of cyberattacks.
- Enhanced Compliance: Webwatcher software can help organizations comply with data privacy regulations by providing insights into user activity and ensuring that sensitive information is protected.
Case Studies of Webwatcher Software Use
Webwatcher software has been employed in various contexts, offering insights into its practical applications and raising crucial ethical and legal considerations. Examining real-world cases reveals the multifaceted nature of this technology and its potential impact on individuals and society.
Use of Webwatcher Software in Schools
Webwatcher software has been implemented in schools to monitor student online activity, aiming to protect children from harmful content and cyberbullying.
- In the United States, several school districts have adopted web filtering and monitoring systems to block access to inappropriate websites and track student internet usage. These systems can record browsing history, search queries, and even social media activity.
- The use of webwatcher software in schools has sparked debate about student privacy and freedom of expression. Some argue that monitoring student online activity infringes on their right to privacy and restricts their ability to explore different perspectives online.
- Others maintain that such measures are necessary to protect children from online risks and ensure a safe learning environment. The ethical and legal implications of school-based webwatcher software are complex and require careful consideration.
Use of Webwatcher Software in the Workplace
Webwatcher software is also used in the workplace to monitor employee internet usage and ensure productivity.
- Companies may use webwatcher software to track employee websites visited, emails sent and received, and applications used. This data can be used to assess employee performance, identify potential security risks, and enforce company policies.
- The use of webwatcher software in the workplace has raised concerns about employee privacy and the potential for misuse. Employees may feel that their online activity is being excessively monitored, leading to a decrease in trust and morale.
- Legal issues related to employee monitoring vary depending on jurisdiction. In some countries, employers are required to inform employees about the use of webwatcher software and obtain their consent.
Use of Webwatcher Software in Parental Control
Parents often use webwatcher software to monitor their children’s online activity and protect them from harmful content.
- Parental control software can block access to inappropriate websites, limit screen time, and track child’s online activity. It can also be used to monitor social media interactions and prevent cyberbullying.
- While parental control software aims to protect children, it can also raise concerns about over-monitoring and invasion of privacy. Some argue that it can create a sense of distrust between parents and children and limit their online freedom.
- The ethical and legal implications of parental control software are complex and require careful consideration. It is important to find a balance between protecting children and respecting their privacy.
Conclusion
As technology continues to evolve, the role of webwatcher software in our digital landscape will likely become even more complex. Balancing the need for security and privacy with the potential for misuse will remain a critical challenge. Ultimately, responsible use of webwatcher software requires careful consideration of its ethical implications and a commitment to transparency and informed consent.
Webwatcher is a powerful tool for monitoring online activity, but it’s important to remember that your computer’s performance can impact its effectiveness. If you’re experiencing slowdowns or crashes, consider using a pc cleaner to optimize your system. A clean and efficient machine can help ensure that webwatcher runs smoothly and provides accurate insights into your online behavior.
